T6 - Secure OS and TEE
Empowering security applications and scenarios, building security device terminals
T6 - Secure OS and TEE

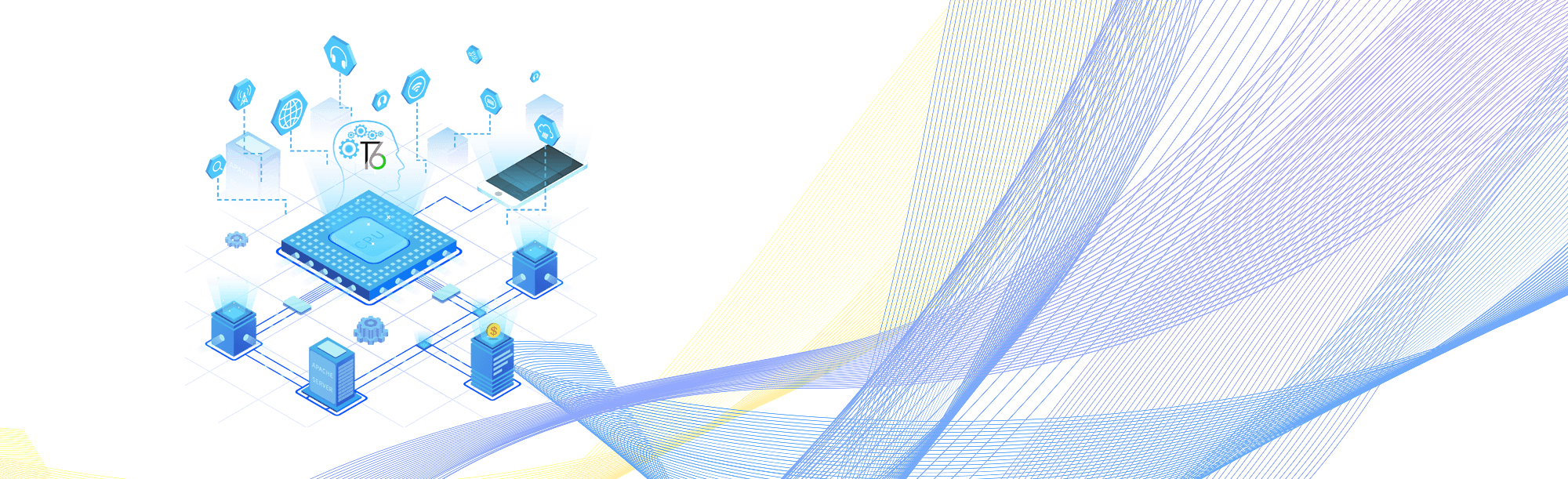
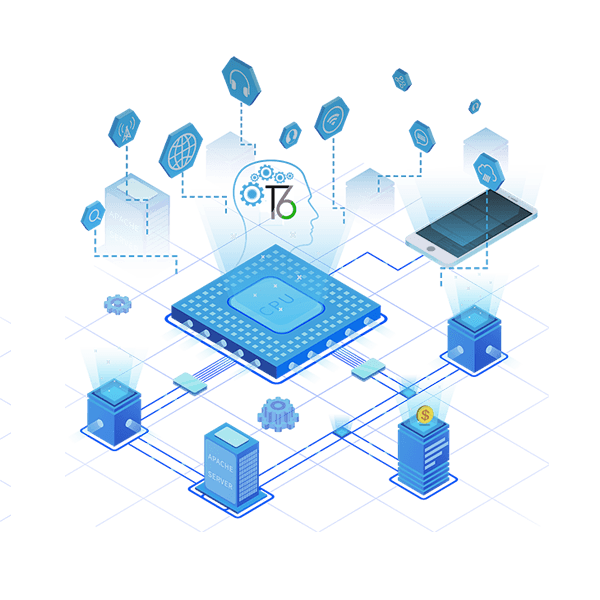
T6 is a secure operating system and a trusted execution environment (TEE) platform designed and developed by TrustKernel since 2012. By design, T6 has leveraged hardware-grade isolation technology (ARM TrustZone, Intel SGX) and the advanced protection mechanisms of modern operating systems to effectively prevent sensitive information from advanced hackings. It ensures the openness and hardware-grade security of operating system itself and applications, biometrics, documents and passwords it hosts. T6 is mainly targeted at smart devices, PCs, servers, and the Internet of Things. By running with legacy operating systems (Android, Linux, etc.) simultaneously, T6 builds a secure system infrastructure in the existing open ecosystem. Now T6 has been widely deployed in Android phones, tablets and IoT devices.
Features Of T6
Tools Of T6
T6 SDK:TKCore
TKCore is a development environment for developers compatible with the T6 platform, for the development and integration of trusted applications. The SDK provides sophisticated development compilation tools and documentation that can help developers build trusted applications within a day. It also provides developers with 1-2 days of development and training programs to help developers speed up the development, testing and deployment of trusted applications.
T6 Mass production line tools: KPH
Key Provisioning Hub (KPH) is the TEE security key provisioning, certificate import and upload tool provided by TrustKernel to the device manufacturers. Through the self-developed (Hub) systems, device manufacturers can easily integrate KPH to the existing production line tools and stations, without changing the existing system of production line or adding additional stations and human maintenance. The production line tool has been widely deployed in dozens of device factories.
Case: trusted application deployed on T6
T6 has the ability to protect the security system for a wide variety of trusted applications. Here are some of the trusted applications that are commonly used by device manufacturers on T6.

Device unlock through fingerprint and iris identification
Identification and device unlocking based on biometric identifications such as fingerprint and iris have been widely used in smart devices, and these applications have been secured by T6.

Secure mobile payment
Sensitive operations such as key protection of mobile fingerprint-based secure payment and payment token signature protection in WeChat, Alipay etc., are operated in T6.

Android security reinforcing
With higher security level and stronger security capability, T6 greatly improves the security of the overall system by monitoring the key logic of the Android kernel in TEE.

SoftSIM
The premise of SoftSIM’s replacing physical SIM is security concern. TEE can ensure the security of SoftSIM and the normal operation of the business.
Secure private space
Secure private space is an innovative application by TrustKernel. Through building a TEE Shadow Space in the Android system, it provides users with a private application operation and file storage space.

Secure locking and unlocking of device communication
Through the implementation of TEE's security management capabilities, device vendors, operators, and companies can perform detailed security management of terminal equipment's communication capabilities.
T6-M: Further defense against advanced physical attack
Physical attacks are a big threat to mobile devices. The portability of mobile devices also makes it vulnerable to theft and loss. In a complex attack mode, an attacker can start an attack on a crypto disk that stores user's data. The attacker obtains the encryption key and successfully decrypts the disk. The current TEE and security operating system cannot withstand such attacks. Therefore, it is important and urgent to protect confidential data in storage from physical attack. In T6-m, all external storage is encrypted, so there is no data leakage under physical attack.
T6-m is the secure enhancement of T6 TEE and protects TEE from physical attacks. T6-m can resist physical attack by eliminating the dependence on external storage. It uses specialized memory encryption techniques for the entire TEE, including kernel and user-layer applications, without the need for hardware support. The corresponding price is that the overall performance of the secure operating system will be reduced by about half.
Zero plaintext in memory
System-level full protection
Transparent to Trustlets
How to Get T6
For Researchers
We provide a flexible T6 SDK and a ready-to-use hardware platform for researchers to support their research.
For Manufacturers And Enterprise Users
For Manufacturers and enterprise users, we provide T6 as well as security solutions based on T6 in source code form. We can cooperate to have a deep customization on T6.